Protect Servers by Layering Security
Make it harder for hackers to access our servers!
When I first started learning about cloud security, the concept of protecting servers from hackers using a layered security approach was introduced to me. Immediately, I envisioned this concept as a big, delicious, moist multilayered cake. The server is the plate that the cake sets on and in order to get a slice of this cake, I need to cut through all of the layers to get down to the plate. Obviously, I love good cake and each time layered security is discussed, I must confess that I think about getting a slice of imaginary cake.
The benefits of layering security to protect our servers is fairly obvious as well. We should never allow a hacker to easily assess our servers. The more layered security measures are deployed on each component and throughout our network, the harder it would be for servers to be compromised. Below are some security measures that should be used. This is by no means an exhaustive list nor does it provide detailed information on each measure. It's just a basic look at security measures in order to facilitate important discussions and considerations as it pertains to this topic.
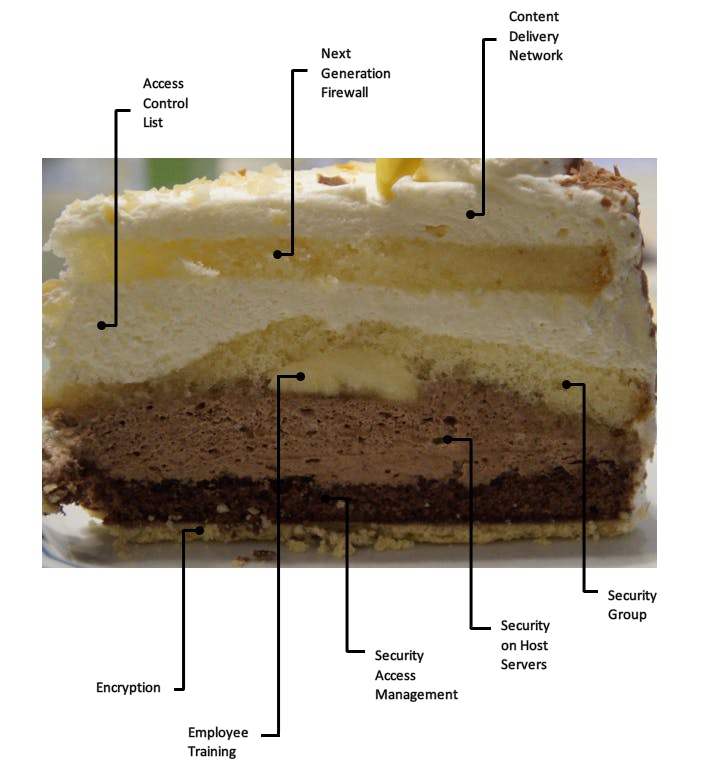
Content Delivery Network
As mentioned in my last blog post, Content Delivery Networks (CDNs) provide beneficial protection against Distributed Denial of Service attacks (Ddos) to origin servers. Services and resources can be deployed at CDNs to detect and mitigate Ddos attacks.
Next Generation Firewall
Firewalls serve as the first line of defense for our networks housed within physical data centers. It monitors our system and blocks unwanted traffic and traffic from unrecognized sources. A firewall is looking for hackers, malware and other malicious activity. Next Generation Firewalls are more sophisticated firewalls that are equipped with Intrusion Protection/Intrusion Detection capabilities which block advanced malware and other evolving security threats.
Access Control List
Access Control List are boundaries configured to protect the subnets of our network. Each access control list is applied to all servers within that specific subnet. There are inbound and outbound rules which can allow or deny traffic. The rules are numbered and evaluated in order from lowest to highest. Therefore, the rules should be created carefully and tested against the user's intentions.
Security Group
Security Groups are boundaries within our subnets, at the server level which should be configured to protect access to servers. There are inbound and outbound rules. However, the rules can only allow traffic to enter a server; there isn't a deny function. The numbering or order of the rules doesn't matter. A user merely needs to allow the traffic that is wanted into a server.
Security on Host Servers
Security measures at this level are directly attached to or implemented on our host servers. These measures include Host Based Firewalls, Patching for Updates, Disable Unnecessary Services and Installing Malware and other protection directly to a server. These measure should be deployed on each server within our network.
Security Access Management
Security Access Management is a service which provides for Authentication, Authorization and Accountability (AAA). If a hacker gains access through all of the previous layers, it could just come down to user credentials! AAA simple works to determine who the user is, what the user has permission to do and tracks the user's actions. This service also provides for connections and access between various servers, services and resources. AAA is an important service which requires competent and expert management in order to secure our servers.
Encryption
Encryption is the "process of encoding information, which is conversion of original representation of the information, known as plaintext to an alternative form known as ciphertext". That is the Wikipedia definition - meaning that when encryption is used, no one can decipher data. This is crucial because private, sensitive or classified information is found on every server in business and home environments. Encryption at rest and in transit is non negotiable when it comes to security considerations. Encryption protects our online privacy, prevents hackers from stealing our personal information and helps businesses adhere to regulatory requirements and standards.
Employee Training
In the midst of all of the security measures mentioned above is Employee Training. Employees, employers and administrators need periodic but routine training in security. How a user should secure their devices, work areas, physical access to the workplace, emails and the like are crucial! Social engineering scams are increasing by the day. Users need to remain aware and cautious about these scams that appear in the form of emails, phone calls and other people.
Now, Back to the Cake
We may not be able to absolutely prevent hackers from accessing our servers all of the time. However, we can make it much harder and while we are sitting back eating a huge slice of delicious cake, we can enjoy it knowing that we did our absolute best by taking a Layered Approach to Security.
For further consideration on this topic, check out this video by my instructor and mentor, Michael Gibbs, CEO of Go Cloud Careers youtu.be/BmF8axtpiBQ
-written: 2/13/22 revised: 2/22/22